🔒Blue Team Resources📘

- Incident Response🔍
- Cyber Threat Intelligence👓
- Packers
- General📑
- Security Community Sites📰
- URLs to Malicious Files
- Linux commands for jumpstarting an investigation
- Ransomware Decryption Tool Lookup
- Linux commands for jumpstarting an investigation
- Ransomware Decryption Tool Lookup
Incident Response🔍
- Gerald Auger’s Cheatsheets
- Awesome Malware Analysis
- Awesome Incident Response
- Awesome Threat Detection and Hunting
- https://otx.alienvault.com/browse/global/indicators
Sandboxing/File Analysis📂
- https://www.hybrid-analysis.com/
- https://cuckoo.ee/
- https://www.threatminer.org/domain.php?q=yahoo.com
- https://capesandbox.com/
- https://analyze.intezer.com/?tab=url
- https://www.joesandbox.com/#windows
- https://evasions.checkpoint.com/
- https://research.checkpoint.com/
- https://attackerkb.com/
- https://exchange.xforce.ibmcloud.com/
- https://virustotal.com
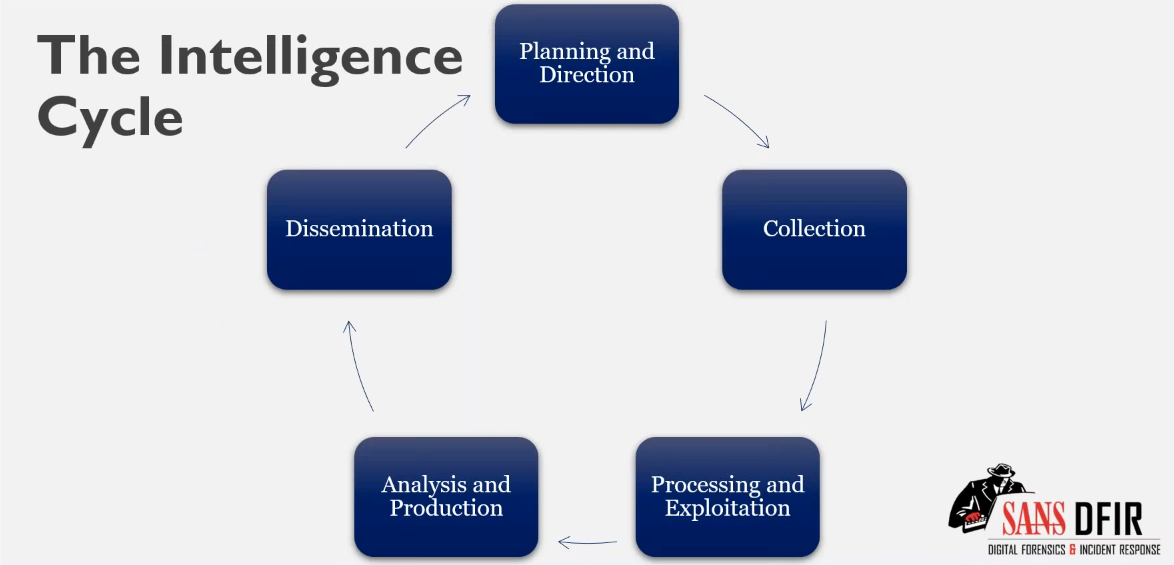
Cyber Threat Intelligence👓
- https://github.com/hslatman/awesome-threat-intelligence
- Diagram:
Packers
- https://www.oreans.com/Themida.php
- https://upx.github.io/
- https://vmpsoft.com/
- Unpacker: https://github.com/horsicq/Detect-It-Easy
General📑
- Awesome Info Sec
- Awesome Python
- Awesome Container Security
- Awesome SOAR
- Awesome Forensics
- Other Security Awesome Lists
- SANS Blue Team: https://wiki.sans.blue/#!index.md
- https://labs.f-secure.com/tools/
- https://isc.sans.edu/forums/diary/FLOSS+20+Has+Been+Released/28776/
- https://hauptsec.xyz/OSCP/proxychains/
- https://app.netlas.io/
- https://www.ericconrad.com
- https://www.honeynet.org/projects/old/capture-bat/ (monitor the state of a system during the execution of applications and processing of documents)
- https://www.loldrivers.io/
- https://gtfobins.github.io/
Security Community Sites📰
- Fortinet Blog: https://blog.fortinet.com
- Naked Security: https://nakedsecurity.sophos.com
- Securosis Blog: https://securosis.com/blog
- Uncommon Sense Security: http://blog.uncommonsensesecurity.com
- Schneier on Security: https://www.schneier.com
- Krebs on Security: https://krebsonsecurity.com
- StackOverflow: https://stackoverflow.com/questions/tagged/security
- Portswigger: https://portswigger.net/daily-swig/vulnerabilities
- TrendMicro: https://www.trendmicro.com/vinfo/us/security/news/
- ThreatPost: https://threatpost.com/
- Security Week: https://www.securityweek.com/
- Bleeping Computer: https://www.bleepingcomputer.com/news/security/
- The Hacker News: https://thehackernews.com
- https://isc.sans.edu/diaryarchive.html?year=2022&month=6
- VulnDB: https://vuldb.com/?updates.202205
- https://www.redpacketsecurity.com/daily-vulnerability-trends-8-5-2022/
URLs to Malicious Files
- urlhaus.abuse.ch/
- bazaar.abuse.ch/browse/
- https://www.malware-traffic-analysis.net/index.html
Linux commands for jumpstarting an investigation
- strings, file, ss and ps
Ransomware Decryption Tool Lookup
- https://www.nomoreransom.org/en/decryption-tools.html
Jump Lists
- https://binaryforay.blogspot.com/2016/03/introducing-jlecmd.html
Linux commands for jumpstarting an investigation
- strings, file, ss and ps
-
strings second_version -n 32 grep -E ‘^[a-z0-9]{32}$’ //-n {x} option means filter words less than x in length - string -e //encoding
Ransomware Decryption Tool Lookup
- https://www.nomoreransom.org/en/decryption-tools.html
